Preparing for Cyber attacks
Part 2 of 2
In our last blog post , we discussed a presentation from our partner KnowBe4 on the evolution of cybercrime attacks and current methods that hackers are using to gain access to your personal and/or company information. In this second post, we will discuss what exactly you can do to ensure you and your company stay safe from cyber attacks moving forward.
So what can we do?
Maximize protections:
- Switch from ESET Antivirus to ESET Endpoint Security (need to pay attention to the policy, it does a lot more than AV)
- Add additional email security measures:
- Barracuda ESS
- Office 365 ATP (SafeLinks, SafeAttachments, Spoofing protection)
- Use firewall security services such as:
- Sonicwall Advanced Threat Protection
- Fortigate FortiGuard
- DPI-SSL if possible
- Enable Multi Factor Authentication on all accounts:
- Office 365
- Remote access (Sonicwall can do Time-based One Time Passcodes via authenticator apps)
- Set up Data Loss Prevention tools in Office 365 to prevent account numbers, Social Security Numbers, and other sensitive data from being emailed. You could also consider least automatically encrypting such things and triggering a warning email when such data is potentially being emailed or accessed.
- Enable Conditional Access rules on Office 365 accounts (requires Azure AD Premium P1 license)
- Ensure only specific countries have access, and block access from specific countries that are known for cybersecurity attacks.
- Majority of ransomware attacks happen from Russia or surrounding area
- Minimize the number of administrator accounts, and maximize the administrator account password length and complexity
- Encourage clients to get Cyber Insurance that covers ransomware
- Set up Azure Sentinel SIEM for all Office 365 customers
- Azure Sentinel ingests and analyzes Office 365 logs for free, so you can see what is happening within your email system and all documents
- Configure any alerts triggered by any of the above items to go somewhere that’s monitored and won’t go unnoticed for days
- Do not use a direct remote desktop, use a Virtual Private Network (VPN) or Remote Gateway to access your remote desktop
Patch machines:
- Schedule monthly maintenance windows to install Windows Updates on all servers, but especially on publicly accessible machines that are used by different people regularly
- Make sure all workstations are getting Windows Updates regularly to avoid software and programs from becoming outdated and vulnerable to attacks
- Scan networks for old versions of software (Java and Flash are especially bad) using Lansweeper, then updated any outdated software and programs
- There are more powerful (and costly) scanners like Rapid7 Nexpose that generate reports of vulnerabilities per machine
Protect backups:
- Take backup server off of Active Directory
- Take backup repository off of Active Directory
- Encrypt backups that are both local and offsite
- Use complex passwords for both server and repository
Train users:
- Every staff member and user should at least have some sort of annual required security training
- KnowBe4 Subscription with monthly phishing tests, yearly training, new hire training
- Depending on the subscription level you choose, you can automatically move failed testers into further training or escalate to managerial notifications so managers can be sure
- KnowBe4 Subscription with monthly phishing tests, yearly training, new hire training
Is Your Business Safe?
Mission Critical Systems can help you find and correct the digital vulnerabilities that your business may have with the recommendations found in the network security assessment. Cybercrime costs businesses more than $6 TRILLION every single year, and the threat is growing every single day.
Don’t let it happen to your business. Before it becomes a problem for you, make sure that you are protected and prepared. Mission Critical Systems offers cyber security and network security assessments which cover over 80% of what full network security audits cover and are available at a fraction of the cost to find vulnerabilities within your IT infrastructure and provide solutions to keep your business secure. We’ve also put together a great infographic to help keep in mind the protocols you should have in place for your IT Security:
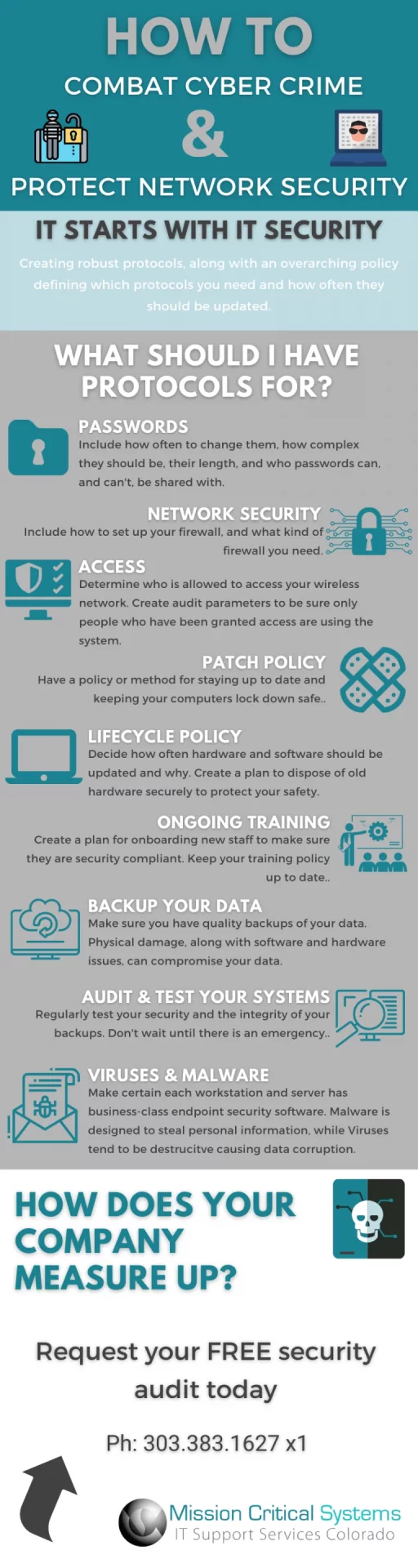
Fill out our security assessment request form today and see how safe your business really is. Our professional staff has extensive experience in helping businesses just like yours become digitally secure. If you already have an MCS consultant, reach out to them today to strategize on solutions that address these areas.



